Continuous TSCM
There are many ways for bad actors to exfiltrate information from an organization. For example, covert transmitters can create voice or data channels that are difficult to detect. These devices commonly use wireless protocols at unmonitored frequencies. For data exfiltration, cellular protocols are the most prevalent example of an “out-of-band” network that can move large amounts of data. Organizations are finding it harder and harder to monitor the entire radio frequency spectrum of protocols and bands for anomalous and/or high volume exfiltration signatures.
THE PROBLEM
Surveillance devices are becoming cheaper and easier to access. There are countless numbers of inexpensive bugs, pwn plugs, and listening devices that can be purchased over the counter and over the Internet. They can be installed, have their own computers, and have their own cellular backhaul prepaid chips.
These devices are not going over the wire, through normal security teams' monitoring systems. Instead, the devices backhaul the data through unmonitored protocols.
Surveillance vulnerabilities Include:
Rogue Wireless Devices and Networks being used for Data Exfiltration
Typical exfiltration prevention techniques involve monitoring corporate networks and preventing the use of USB ports for storage. However, by utilizing cellular or other “hard to see” protocols, attackers can bypass these controls
Nefarious devices such as pwn plugs and pineapples are left to specifically steal data and backhaul that data out over cellular
Unauthorized video systems planted in an organization
THE REQUIREMENTS FOR A continuous TECHNICAL SURVEILLANCE COUNTERMEASURE SOLUTION
A Continuous TSCM security solution needs to:
Provide visibility into the wireless networks, traffic, and devices operating in your environment,
Inform you of the attack surface for each of these devices,
Alert on active wireless attacks on those devices through your existing SIEM systems, and
Suggest best practices for minimizing the attack surface and mitigating an attack in action,
Operate 24x7 to catch out-of-hours transmission of data
Specifically, a solution must:
Detect all devices operating in the wireless spectrum, to include but not limited to, Wi-Fi, cellular, Bluetooth, and the hundreds of other protocols in the Internet of Things (IoT)
Detect current and future protocols without requiring hardware upgrades
Detect known and unknown emitters via observing energy patterns
Provide awareness of any wireless threats including active attacks and rogue networks
Detect data exfiltration via wireless devices
Be always on
Detect unauthorized devices
Detect vulnerable devices being installed
Detect anomalous wireless activity originating from the campus
Alert on a wireless attack surface introduced by the installation of new equipment
Detect rogue cell towers which can send signals into your facility
What kinds of organizations need this solution?
Fortune 2000, government, financial services, technology, and other organizations with sensitive data or high risk areas
Bastille Solution
Bastille provides intelligent and comprehensive, continuous monitoring for wireless threats within your secure locations. The Bastille solution is a combination of Sensor Arrays deployed throughout your facility, Concentrators to aggregate and process sensor data, and the Fusion Center platform which collects and analyzes wireless data and is the central integration point which can be connected to, and augment, your security monitoring system with Bastille’s wireless threat data. This tiered architecture allows the Bastille solution to scale from monitoring a single room to many campuses across the world with a single management interface.
Figure: Bastille’s Continuous TSCM solution.
Sensors
Comprehensive monitoring is achieved through deployment of Bastille’s sensor arrays throughout your facility. Bastille sensor arrays detect wireless activity from 25 MHz to 6 GHz and this RF traffic is decoded, processed and sent to the Bastille Concentrator for further event correlation. The sensor arrays are 100% passive, which means they never transmit and do not have any moving parts to reduce component failure and perform silently. The sensor arrays are plenum rated and are available for indoor or outdoor use.
The sensors capture all available attributes of the wireless devices including dozens of identifiers such as vendor name, Bluetooth network definitions, Wi-Fi device characteristics, and Cellular network information. Bastille’s Sensor Arrays are based on Software Defined Radio (SDR) technology which allows them to receive in-place upgrades ensuring future protocol support and decoding.
Concentrator
The Bastille Concentrator receives data from all of the sensor arrays in a facility, refines and consolidates the data into events, and sends them to the Fusion Center. The Premium Concentrator is used to gather additional data from cellular device transmissions.
Fusion Center
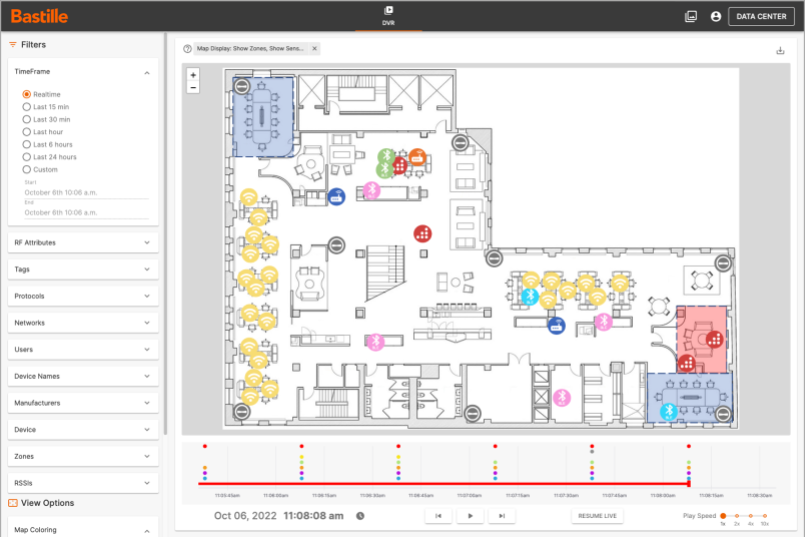
Bastille’s Fusion Center platform receives wireless data from the sensor arrays, compiles and analyzes the data, and displays all data on current and historical wireless device activity. Bastille’s Fusion Center is the only Common Criteria / NIAP certified product in this industry and provides you additional assurance on the quality and security of the Bastille solution. Any detected wireless device is clearly overlayed on your facility floor plan, including current device location to within 3m accuracy and a playback capability to show the historical location of each wireless device as it moved through your space. This playback functionality allows correlation with other systems to determine who brought the device in, along with when and where they traveled in the facility.
Bastille’s Fusion Center automatically detects known wireless threats from its curated database of threats discovered by Bastille’s Threat Research team and industry disclosed vulnerabilities. The Fusion Center platform offers highly customizable reports, provides rich API capabilities for integration with SIEM/SOAR systems, and is fully maintained and supported by Bastille along with the sensor arrays for the life of the subscription.
Figure: Device locations plotted on your floor plan
Examples of Bastille’s Differentiation
Bastille has 30 patents in the wireless detection field and maintains significant advantage in detecting wireless threats.
Threat Signatures & Event Intelligence
Bastille’s Threat Signatures filter through all detected devices and apply categorizations to them so you can focus your resources on the critical threats. Bastille’s solution brings wireless data to your security policy enabling you to evolve your policy to match the reality of your environment.
Advanced Bluetooth Device Detection
Bastille’s unique approach simultaneously monitors all 79 Bluetooth channels and 40 Bluetooth Low Energy channels. This approach identifies Bluetooth paired devices, explicitly noting the paired network endpoints, attributes of both ends of the pairing, and Bluetooth devices performing inquiries or scans. Other vendors only show when Bluetooth devices are looking to pair; after they’ve paired they become invisible. After a device is paired is when it has the capability to exfiltrate data and cause disruption; you need this visibility to protect against Bluetooth surveillance threats.
Individual Cellular Device Detection
Bastille provides comprehensive data on individual cellular devices which transmit in the monitored space. With Bastille’s technology, you can track the location, carrier, and specific attributes of each cellular device as it moves through the monitored facility.